Blockchain Threat Intelligence & Cybersecurity
Exploring the integration of big data, artificial intelligence, and blockchain technologies to advance cybersecurity threat intelligence and defense strategies.
The Future of AI-Powered Cybersecurity
Using big data, artificial intelligence, and the blockchain, HEROIC is powering the next generation of cybersecurity.
Cybersecurity Is Broken
Threats are always two steps ahead

Security threats and attacks are increasing at exponential rates year over year
Current cybersecurity solutions are outdated and ineffective against attacks
Threat data continues to be controlled by large entities and governments

The cybersec industry is facing a shortage of 3+ million personnel by the year 2021
Solution: Decentralized Cybersecurity Powered by Artificial Intelligence
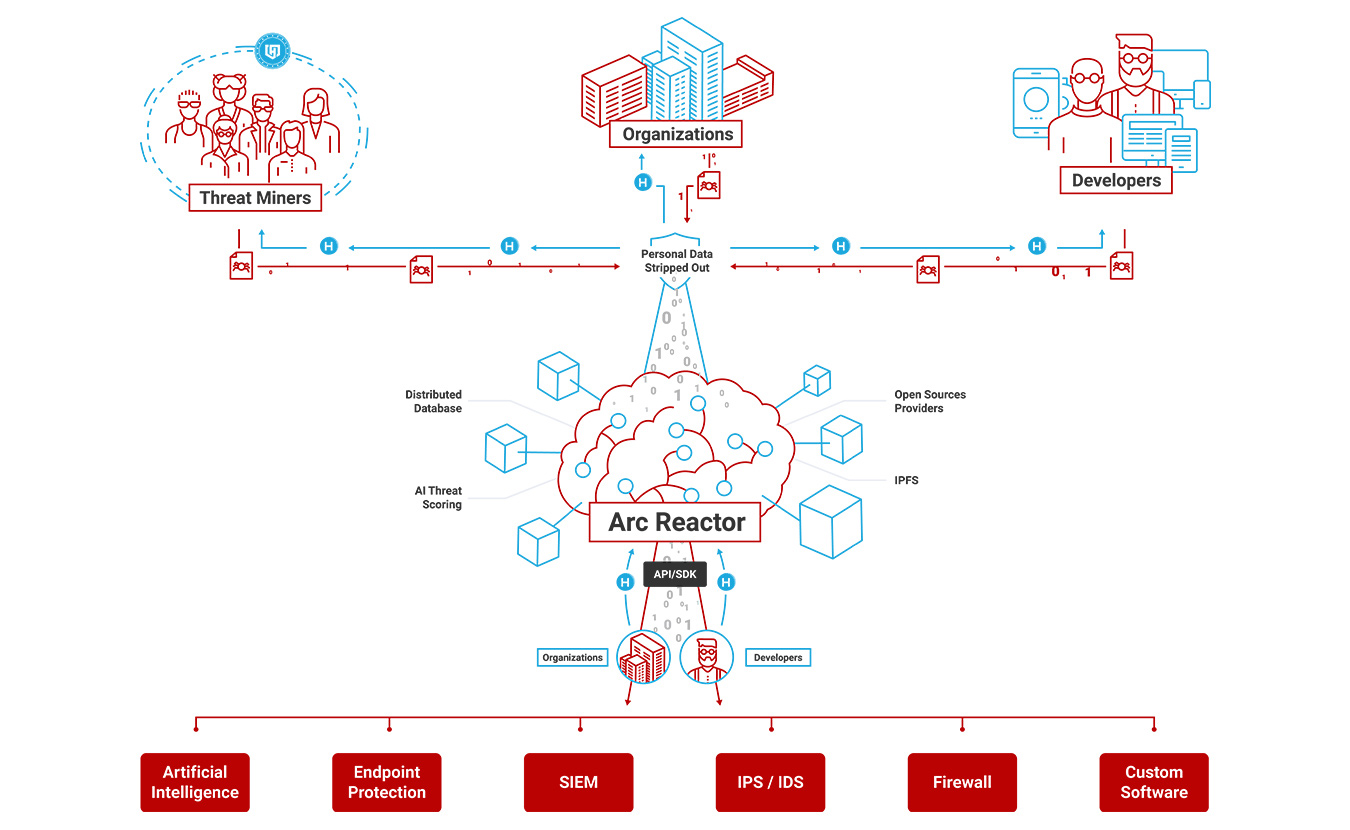
Arc Reactor

Guardian
R&D Platform
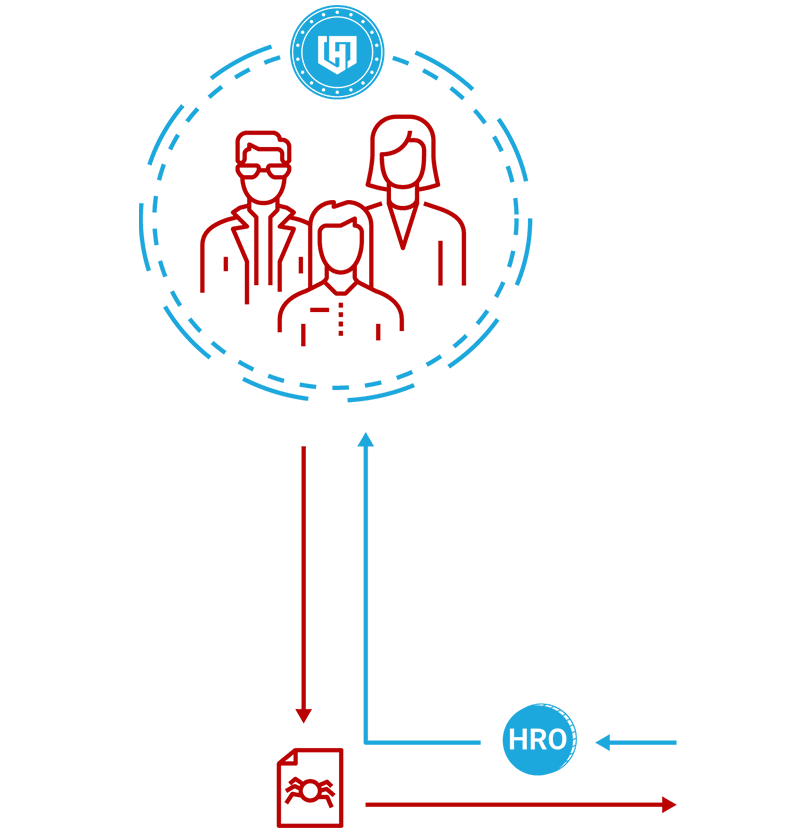
Threat Miners (Individuals)
Threat miners receive intelligent threat protection while allowing their devices to anonymously become part of the HEROIC Ecosystem. Miners participate by running the threat protection software on their devices and using it in normal everyday activity. Encountered threats seamlessly pass through an anonymity shield to strip any personally identifying information and are then shared to Arc Reactor for the greater good of the community. As threat miners encounter, verify and contribute threats, they receive compensation for their contributions in the form of HRO tokens.
Benefits for Threat Miners:
- Intelligent Threat Protection
- Compensation for participation on the network
- Access to HEROIC Guardian
- Protection for Devices and Cloud Services
- Help Make the World More Secure
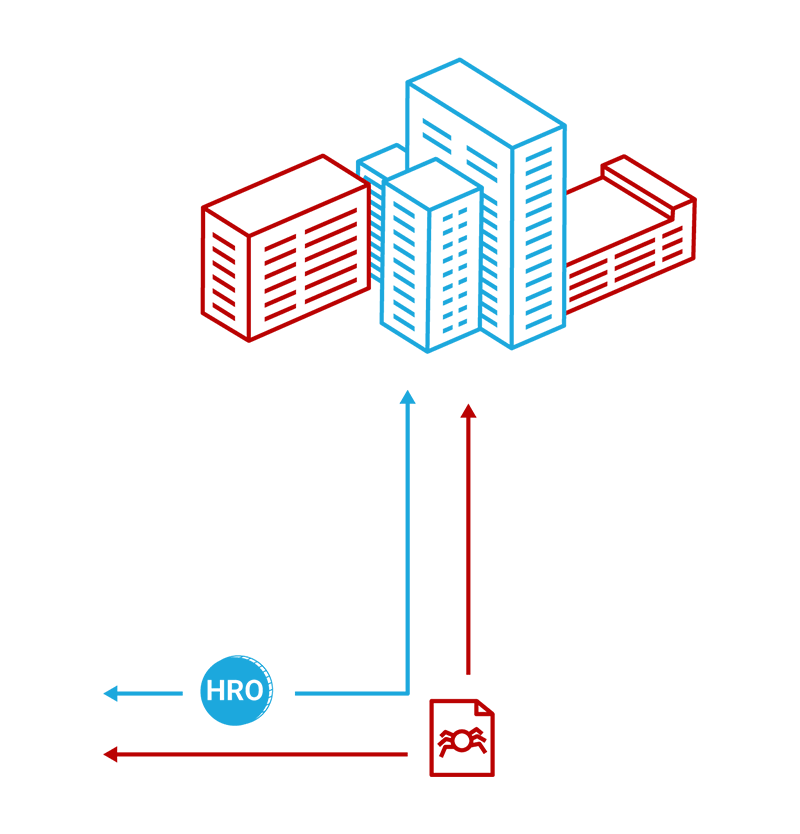
Organizations
Organizations are essential to the HEROIC ecosystem as they contribute vast amounts of threat data and provide for an efficient marketplace of that data. Organizations will have open access to the entirety of the Ecosystem for use in protecting their own data, receiving compensation for contributed data, integrating it with third-party branded products and services, and building their own software. Organizations may include businesses, schools, non-profits, mining-pools, governments and others.
Benefits for organizations:
- Compensation for Data Participation
- Access to Open Threat Intelligence Exchange
- Enhance 3rd Party Cyber Solutions
- Build Custom Solutions and Applications
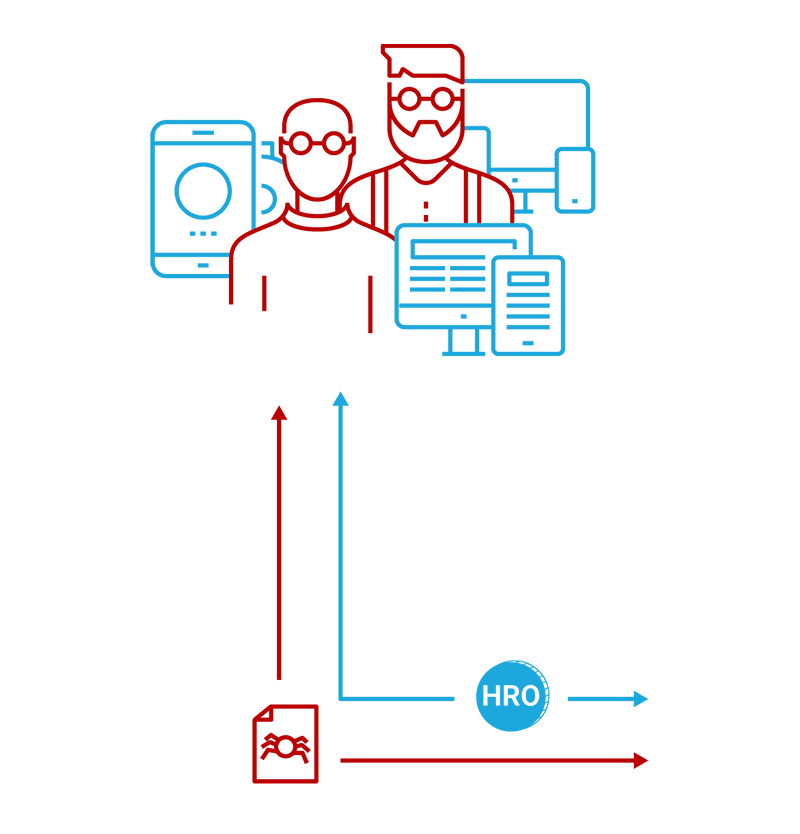
Developers
Developers will have open access to the entirety of the HEROIC Ecosystem. Our R&D Environment will provide the ability to research, develop, test and distribute your own software and algorithms. Developers will be compensated for their creations which will include intelligent algorithms, software tools, and full software systems. Ecosystem compensation is made exclusively through the HRO token.
Additional benefits include:
- Access to threat intelligence repositories
- Robust community of developers
- Ability to research, build and test algorithms
- Revenue stream to devs and security experts
- Compensation for threat-blocking algorithms
- Download and use data for research and products
- Build decentralized applications

Threat Miners
Benefits for organizations also include the following:
- Access to threat intelligence repositories
- Compensation for data participation
- Download and enhance own cyber products
- Build decentralized applications

Organizations
Benefits for organizations also include the following:
- Access to threat intelligence repositories
- Compensation for data participation
- Download and enhance own cyber products
- Build decentralized applications

Developers
Additional benefits include:
- Access to threat intelligence repositories
- Robust community of developers
- Ability to research, build and test algorithms
- Revenue stream to devs and security experts
- Compensation for threat-blocking algorithms
- Download and use data for research and products
- Build decentralized applications
Benefits In Participating
Open, AI-Powered Threat Protection

Threat Compensation
Effortlessly recreive HRO tokens as your devices anonymously share threat data that are gathered as you surf the web, download files and programs and through normal everyday device usage.

Help Protect the World
In The News